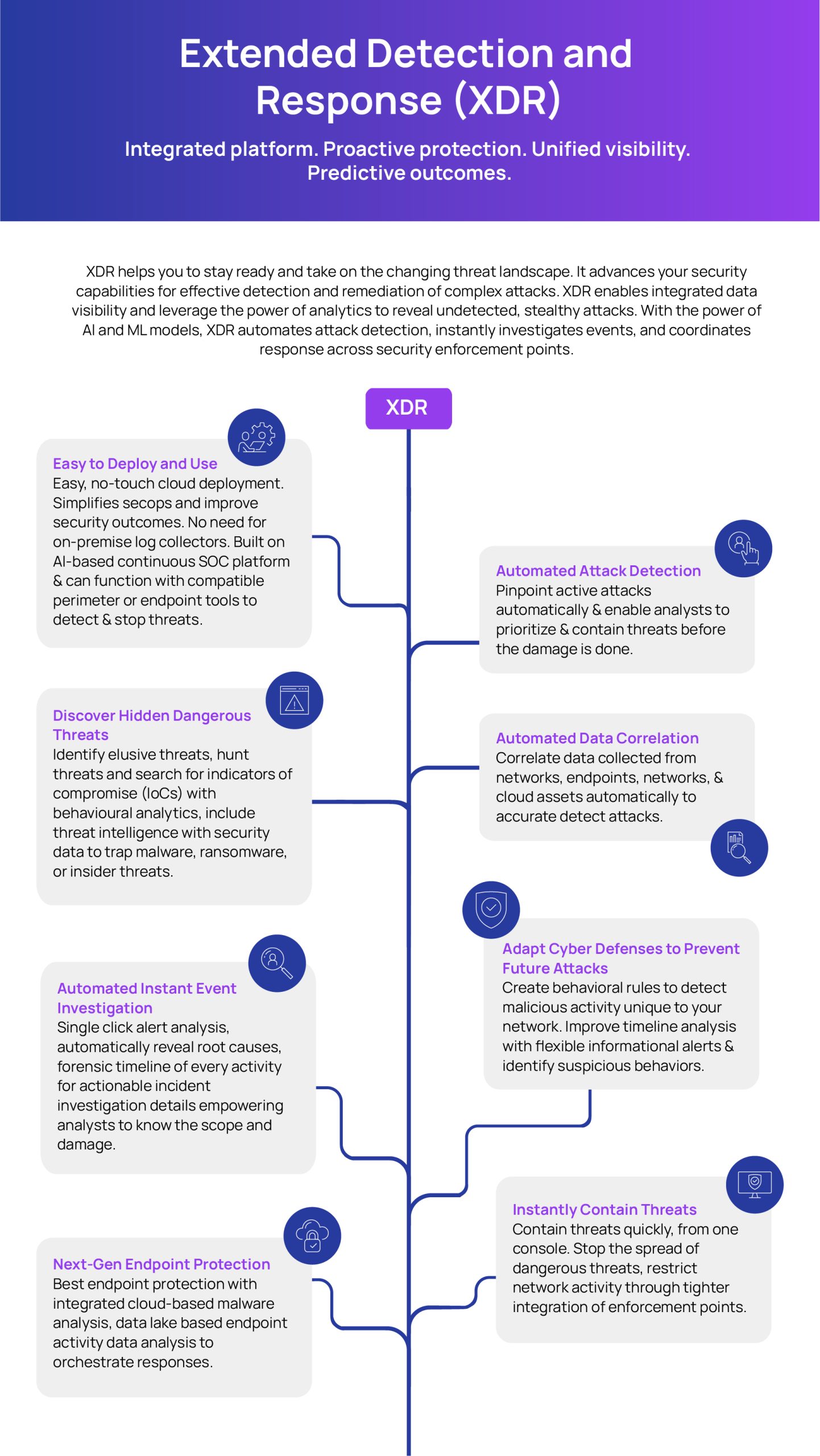
Integrating multiple security technologies is necessary to ensure cohesiveness in security operations. XDR known as Extended Detection and Response, is a platform that consolidates various security solutions and makes intelligent, rapid detection through ML-driven analytics to ensure quick responses.
With adversaries adopting complex maneuvers to breach through legacy security controls, security operations need a platform such as XDR to combat them intelligently. Disjointed security tools or data sets will not work anymore.
XDR is the proven way to reduce false positives, improve analyst productivity, and reduce alert overloads. The platform is threat-centric, wherein it can be contextualized to detect and respond to threats rapidly.
This infographic explains the key features of the XDR platform: