Privacy and data protection has recently become the prime focus for many organizations worldwide. Increasing number of data breaches has eroded customer and consumer trust forcing nation states to establish privacy and data protection rules and regulations. Organizations are moving towards implementing business and technology tied programs to effectively govern, manage and implement enterprise-wide data protection. However, proliferation of technology, advent of new channels for data sharing and dependency on cross border data transfers have made data protection a complex undertaking. Coupled with the absence of data asset inventories and lack of visibility into data flow across internal and external boundaries, organizations face a challenge in implementing appropriate data leakage response strategies and controls. Cross functional buy-in, participation and co-ordination required for program implementation further hampers establishment of an effective data protection control environment.
Introduction
NuSummit Cybersecurity was engaged by a leading Islamic bank for designing and implementing a comprehensive data protection program that aimed to address governance, management and implementation of data protection in a well defined manner.
Client Background and Challenges
As part of its information security program, the client had implemented multiple information security point solutions. Specific to data protection, the client was compliant with payment card industry’s data security standard and had implemented a Data Leakage Prevention (DLP) solution in monitoring mode. The client wanted to expand its data protection initiative into a more comprehensive and holistic undertaking that would allow for enhanced and more effective control environment as well as better value from the DLP solution. Lack of visibility into data that needed to be protected was also a key driver for the engagement and the expectation included enabling the bank to gain a greater visibility into data flow across organization boundaries. Further, the bank was looking to understand the specific initiatives that it should undertake as part of its program implementation.
Business Solution
- Conducted data flow analysis for 25 business processes.
- Conducted data leakage risk assessment.
- Developed a 3-year detailed roadmap with focus areas and actionable initiatives.
- Developed the data classification policy and handling guidelines.
- Developed a data type flow map with representation of controls and gaps across network zones and systems.
- Defined a data protection program structure as well as key performance indicator metrics.
- Assessed the current state maturity in terms of data protection governance, functional areas, practices and controls.
- Created a governance framework with a dedicated data protection organization structure as well as cross functional roles, responsibilities and involvement.

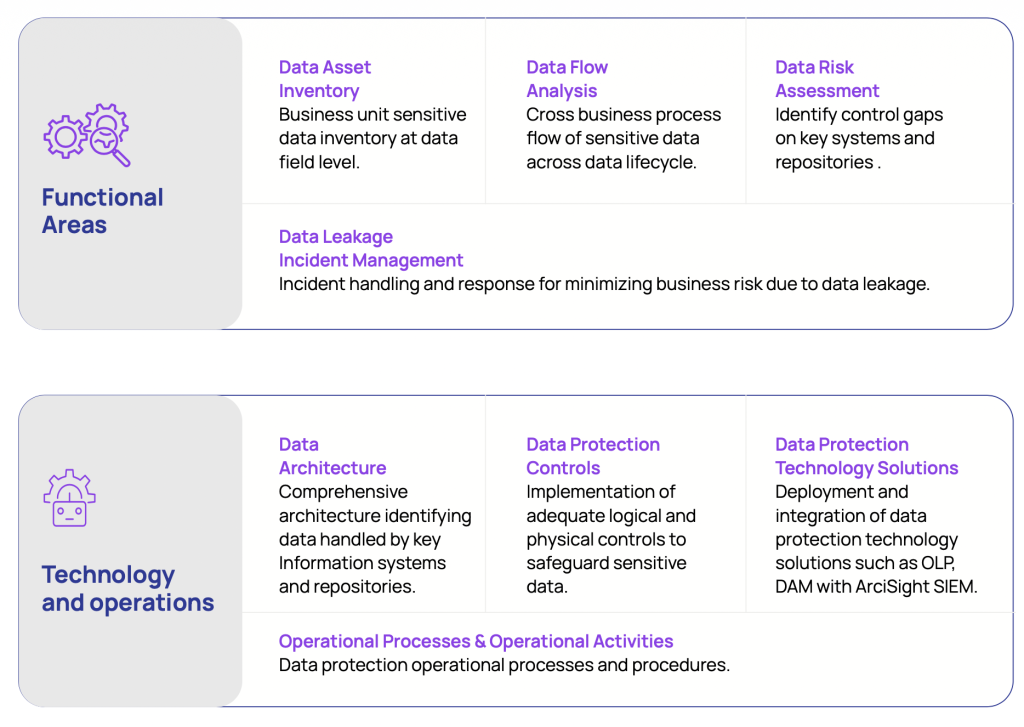
DP Maturity Assessment Framework DP Governance Organization
Data Security Architecture
Our Approach
The engagement was delivered in the following four phases.
Maturity Assessment
- Develop maturity assessment framework aligned with CMMI model and graduated maturity questions to assess current state maturity of data protection areas, practices and controls. Areas covered included: Strategy, Governing Body, Roles and Responsibilities, Policies and Guidelines, Compliance, Training and Awareness, Data Discovery, Data Classification, Data Leakage Risk Assessment, OLP incident management, Process practices (collection, storage, use, transfer, disposal), Controls (systems, databases, applications, communication networks, handled devices), and technology solutions.
- Analyze and validate findings, define to-be-state maturity levels and identify initiative focus areas for program structure and roadmap.
Program Design
- Develop overall data protection program structure.
- Develop a three year roadmap with detailed initiatives based on the finalized program structure and maturity assessment results.
- Design data protection governance organization structure and define roles and responsibilities.
- Develop cross functional interaction RACI model to establish cross functional obligations for each initiative.
- Define classification criteria, scheme, information categorization, classification process and information handling guidelines.
Data Flow Analysis and Leakage Risk Assessment
- Shortlist and prioritize business departments and processes for data flow analysis. Conduct kick-off sessions with key stakeholders.
- Conduct data flow analysis for 25 business processes. Identify data, format, classification, repositories, authorized users and access rights, authorized users by data channel, document keywords, fingerprinting requirements, dLP rules, incident threshold, and monitoring/enforcement mode actions.
- Conduct data leakage risk assessment – identify information systems across data flow, review controls, identify control gaps and determine risk levels. Develop remediation recommendations.
Data Security Architecture
- Develop a comprehensive model to extend data flow analysis and leakage risk assessment and define data security architecture views by data type (e.g. Payroll Data, Credit Card Data).
- Finalize and submit recommendation report for DLP and control environment.
Benefits
- Enablement of cross functional engagement via detailed responsibilities for governing, managing and implementing program initiatives.
- Standardized and repeatable process with well defined operational templates for identifying data, its parameters and flow across business processes.
- Insight into current state and facilitation of strategic program planning based on future state initiatives.
- Enhancement of DLP policy and rules based on data flow and document analysis.
- Practical data classification and information handling guidance.
- Strengthening of data protection control environment.