With time, the enterprise application landscape has gone through an intriguing evolution journey, from monolithic and centralized to eventually becoming fragmented and dispersed. Today, applications have become intrinsic to modern business operations, allowing users seamless access to services and data. This accessibility, however, has also exposed modern applications to newfound cyber threats that include bad actors embracing the latest tech like AI to amplify attack campaigns.
Modern applications’ widespread and connected nature increases exposure to external cyber threats. Additionally, while application security protocols have continued to evolve to address more modern threats, the threats of yesteryear haven’t disappeared but only progressed to adapt to newer defences. The result? Enterprise applications remain as vulnerable as ever.
Research reveals that 83% of applications exhibit at least one security vulnerability during their initial security assessment, and application breaches, including stolen credentials and similar vulnerabilities, account for one-fourth of all violations worldwide[i]. This clearly emphasizes the indispensability of securing applications, especially in a world that is increasingly going digital.
Web Application Firewall (WAF) – The First Line of Defence Against Threats
When it comes to negating web application attacks, Web Application Firewalls (WAF) often serve as the first line of defence. A WAF shields an application by constantly monitoring and filtering the Hypertext Transfer Protocol (HTTP) and Hypertext Transfer Protocol Secure (HTTPS) traffic between the internet and the application. It often employs dynamic security policies such as automatic false-positive correction, API discovery and protection, bot mitigation, application-layer 7 DDoS protection, and more to ensure enterprise applications are secure. WAF can go a long way in blocking some of the most scathing cyber threats without a user knowing. Let us have a look:
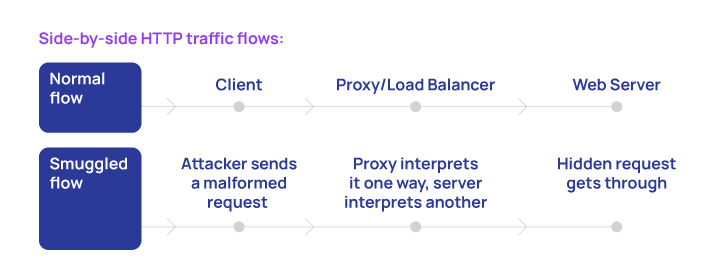
- HTTP request smuggling: Often referred to as HTTP Desync Attacks, HTTP request smuggling is a technique employed by attackers to interfere with how an application running within an ecosystem sequences HTTP requests received from one or more users. It enables the attacker to smuggle a request to the web server without notifying the devices between the attacker and the web server. These attacks are often challenging to negate with the help of conventional security protocols, as attackers can easily bypass security controls to seamlessly interfere with other running user sessions to gain unauthorized access to confidential user data.
Side-by-side HTTP traffic flows:
- Normal flow: Client → Proxy/Load Balancer → Web Server
- Smuggled flow: Attacker sends a malformed request → Proxy interprets it one way, server interprets another → hidden request gets through
- Clickjacking: This is a relatively new threat that often happens on the client side, and its objective is to trick application users into clicking a web element that is different than what it is perceived as. Hackers execute such attacks by hiding malware or code in a seemingly innocuous-looking control within an application, mainly within the JavaScript of third-party services, which often remain unmonitored by standard application security tools or testing. Today, clickjacking is widely used primarily in the financial services industry to direct traffic to a specific application address to collect sensitive information saved on a browser, such as passwords or usernames.
- Injection attacks: Injection flaws, including OS, SQL, NoSQL, and Lightweight Directory Access Protocol (LDAP) injection, have been a staple attack technique for hackers regarding breaching application security protocols. An injection attack occurs when malicious data is injected within an application, often veiled as a query or command. This data tricks the user interpreter into executing commands without the intended purpose or giving access to data without the proper authorization.
- Directory traversal/ file path traversal: A file path traversal attack is essentially a web security vulnerability that allows a hacker to gain unauthorized access to directories and files stored outside an application’s web root folder. These files may include sensitive information such as credentials for back-end systems, application codes, and operating system files. Attackers often execute a file path traversal attack by tricking either the web application or its server into returning files that remain outside the web root folder.
- Predictable resource location attacks: Attackers employ this technique to gain access to an enterprise application’s hidden content. This often involves calculated guesses from the attacker’s end through brute force to accurately guess directory and file names that are not available for public viewing. File name brute forcing is easy for hackers because files/paths such as temporary files, logs, administrative site sections, sample files, demo applications, and back-ups often have similar naming conventions and are stored in standard locations.
A combination of threat combat techniques, such as complete API discovery and protection, built-in HTTP DDoS protection, integrated bot management, and data leakage prevention mechanisms, makes WAF an indispensable aspect of modern applications. When combined with other advanced application security protocols, WAF can be a valuable aid in protecting application security.