In today’s cloud-native world, containers are at the heart of how organizations build, deploy, and scale software. This modern approach offers significant benefits, especially in terms of speed and flexibility, but it also introduces new security risks, especially in large, distributed environments.
With organizations consuming thousands of open-source and internal container images daily, verifying their authenticity, integrity, and provenance has become critical. Simply trusting what’s available in your registry or public repositories is no longer sufficient.
Challenges of the Modern Software Supply Chain
Modern software supply chains face serious security gaps, including three critical issues:
- Unverified images — Containers pulled from registries may be tampered with or contain malicious code.
- Lack of traceability — Teams often can’t prove where a container came from or how it was built.
- Missing visibility — Without a signed Software Bill of Materials (SBOM), it’s impossible to know what’s inside each container image (dependencies, libraries, versions, etc.).
These weak spots make it more likely that corrupt or compromised images slip into production. They also increase the risk of zero-day vulnerabilities and can lead to failures in meeting compliance requirements under frameworks such as SLSA, NIST SSDF, and ISO 27001.
Why Image Signing and SBOM Attestation Matter
Image signing ensures that only trusted, verified container images are deployed to your environments. It acts as a digital seal of authenticity, confirming:
- Who built or signed the image?
- Whether it has been modified since signing.
- Whether it complies with internal or external security policies.
SBOM attestation goes further by attaching a signed, tamper-proof list of all the software components within the image. This helps organizations:
- Quickly find vulnerable dependencies.
- Track software components for compliance.
- Respond efficiently to new security advisories.
When combined, image signing and SBOM attestation shift companies from blindly trusting code to reliably verifying it before deployment.
How Image Signing and SBOM Attestation Work
Here’s how the process typically unfolds:
Image Signing
- Generate or use existing keys — Developers or CI/CD pipelines use a signing key.
- Sign the image — The image’s digest (SHA256) is cryptographically signed using CodeSign sign.
- Store the signature — The signature is uploaded alongside the image in the container registry (either as legacy mode or as an OCI artifact referrer).
- Verify before deployment — Deployments use the verify command to ensure only trusted, untampered images are deployed.
SBOM Attestation
- Attach to the image – The signed attestation is linked to the image digest and stored in the registry as a referrer artifact.
- Verification and traceability – Consumers or deployment systems can validate the attestation to confirm that:
- The SBOM corresponds exactly to the image, and
- The attestation is authentic and unmodified.
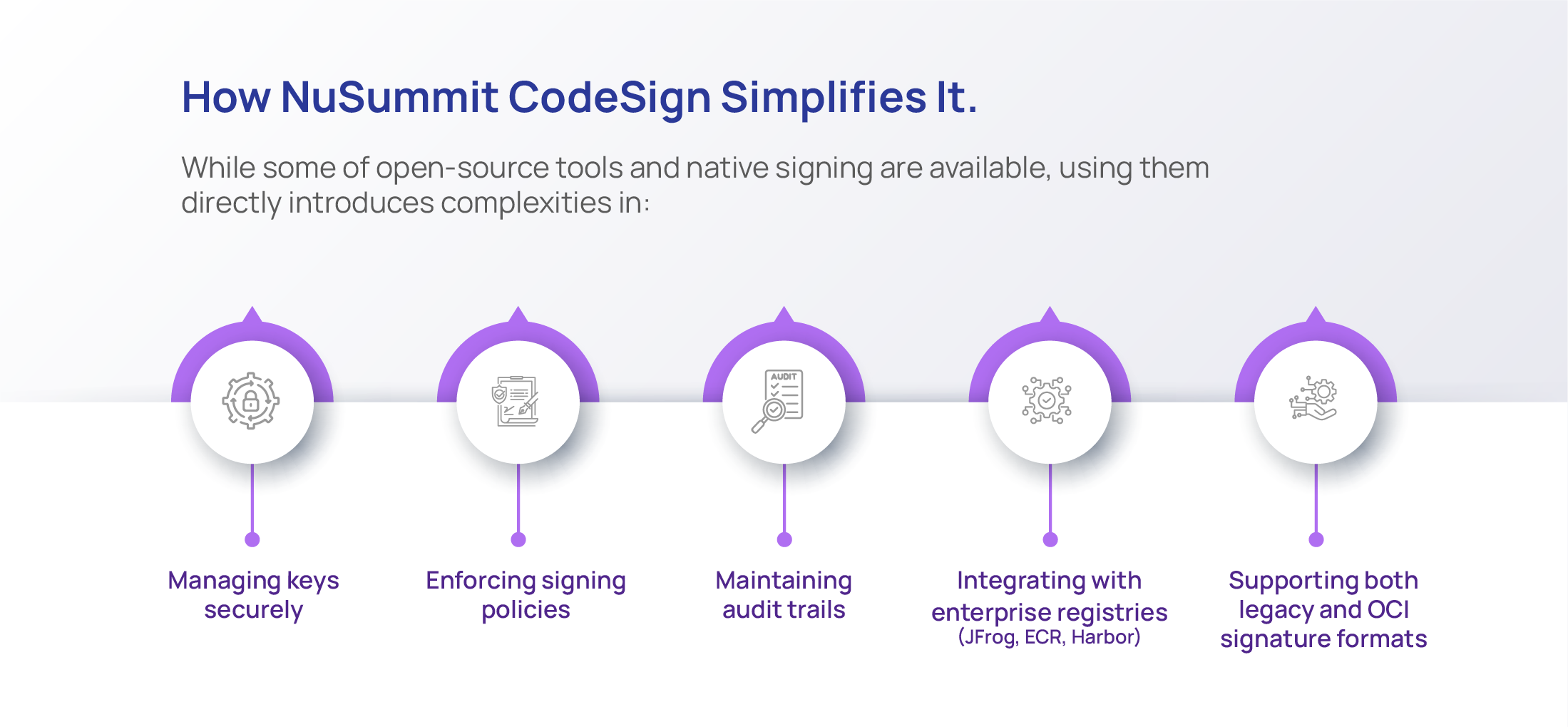
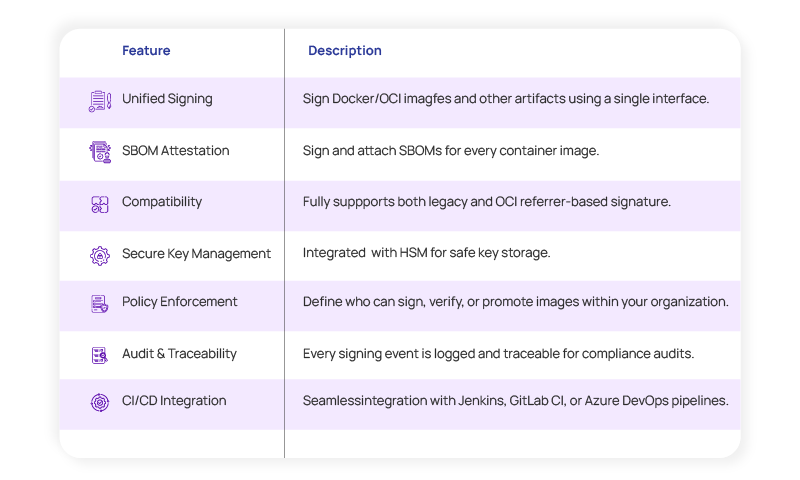
Nusummit’s CodeSign addresses these pain points by providing a centralized, policy-driven platform for secure image signing and attestation. Features include:
How CodeSign Solves the Problem
By integrating signing and attestation directly into your build pipeline:
- Every image that leaves your build system is signed, traceable, and verifiable.
- Only trusted and verified images can be deployed to higher environments.
- Every container carries a verifiable SBOM, ensuring full transparency and faster response to vulnerabilities.
This transforms your container registry into a trusted source of truth, aligning with modern software supply chain security standards like SLSA, NIST SSDF, and CIS benchmarks.
Conclusion
Image signing and SBOM attestation aren’t just nice-to-have features anymore—they’re foundational for securing a modern software supply chain. Enterprise-ready solutions like NuSummit CodeSign give organizations:
- Confidence in every image deployed.
- Compliance with evolving security frameworks
- Full visibility into their software components
Ultimately, this approach protects the entire container ecosystem and ensures only verified, trustworthy images move through your supply chain—from development to production.