Managing identities and access is a key challenge for organizations today. As businesses expand digitally, securing seamless and efficient access becomes increasingly complex. Traditional IAM frameworks often lack the flexibility to meet modern enterprise needs. NuSummit Cybersecurity’s intelligent IAM solutions address this, transforming IAM from a compliance tool into a business growth driver.
IAM Challenges in a Dynamic Environment
For many organizations, IAM remains a necessary but resource-intensive process. Traditional systems often rely on static policies and predefined roles that fail to adapt to real-world complexities. Consider the issues:
- Lack of Flexibility: Static IAM systems struggle to adapt to rapidly changing business environments.
- Inefficiencies in Lifecycle Management: Manual workflows for access requests, approvals, and revocations introduce delays and errors.
- Rising Security Threats: Traditional IAM cannot keep up with evolving cyber threats or provide proactive threat detection.
- Limited Insights: Conventional IAM tools lack actionable data, making it hard for stakeholders to make informed decisions.
These challenges create bottlenecks, leaving organizations vulnerable to security risks and inefficiencies.
Intelligent IAM by NuSummit Cybersecurity
NuSummit Cybersecurity addresses these challenges with an intelligent approach to IAM. By integrating advanced technologies like behavioral analytics, lifecycle automation, and predictive threat detection, NuSummit transforms IAM into a dynamic, context-aware system that goes beyond mere access control.
How Intelligence Enhances IAM
- Precision Through Data:
Intelligent IAM uses behavioral analytics and historical data to tailor access dynamically. This ensures that access decisions are precise, reducing over-provisioning and security risks. - Lifecycle Automation:
Intelligent workflows automate processes like access requests, approvals, and revocations. This eliminates inefficiencies and ensures that users always have the right level of access. - Proactive Security:
With predictive threat detection, intelligent IAM identifies vulnerabilities before they can escalate, offering organizations a proactive stance against security threats. - Actionable Insights:
Real-time dashboards and KPI-driven analytics empower stakeholders with the information they need to make faster, smarter decisions.
What Sets NuSummit Cybersecurity Apart?
In a crowded IAM market, NuSummit Cybersecurity offers a comprehensive, outcome-focused approach. Here’s why customers prefer NuSummit Cybersecurity over competitors:
Intelligence-Driven Precision
Unlike traditional IAM solutions, NuSummit Cybersecurity leverages advanced analytics and machine learning to bring higher accuracy and adaptability. From advanced role modeling to data-driven insights, NuSummit Cybersecurity goes beyond compliance to enhance business agility.
Comprehensive Capabilities
NuSummit Cybersecurity provides end-to-end IAM solutions covering:
- Identity Governance and Administration (IGA): Scalable frameworks for access control.
- Privileged IAM: Robust policies to secure high-risk accounts.
- Application Onboarding: Seamless integration of applications across environments.
- DevOps PAM: Securely integrating privileged access into DevOps workflows.
Tailored Delivery Models
Every business is unique, and NuSummit Cybersecurity understands that. With hybrid delivery models and a Center of Excellence (CoE) for innovation, NuSummit Cybersecurity ensures solutions align with your specific needs.
Proven Expertise
With over 450 IAM projects completed globally, NuSummit Cybersecurity brings a wealth of experience to help organizations navigate the complexities of identity management.
Outcome-Driven Focus
NuSummit Cybersecurity prioritizes measurable outcomes, aligning IAM strategies with business goals to deliver security, operational efficiency, and ROI.
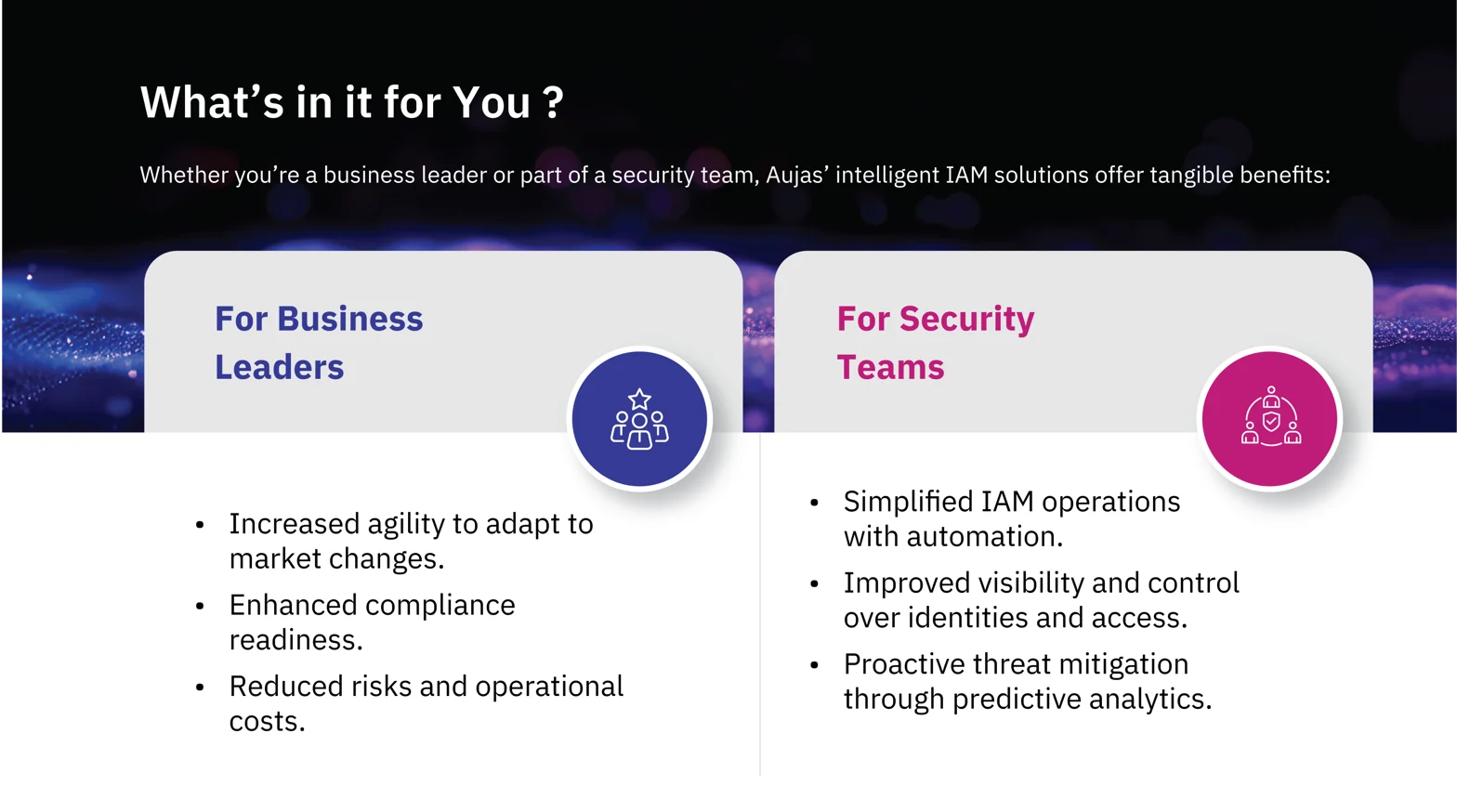
The Future of IAM with NuSummit Cybersecurity
NuSummit Cybersecurity ensures your IAM systems are proactive, ready to tackle today’s challenges and scale for the future. Whether managing complexities or planning, NuSummit Cybersecurity delivers the tools and expertise you need to succeed. NuSummit Cybersecurity’s intelligent solutions ensure that your IAM systems aren’t reactive but proactive, adapting to the challenges of today and tomorrow.