As we head into 2026, CISOs and enterprise architects worldwide are confronting a long-awaited truth: passwords are reaching end-of-life.
For decades, organizations have tried to strengthen passwords through complex policies, password rotation, SMS-based OTPs, authenticator apps, and various multi-factor authentication (MFA) solutions. However, attackers evolved even faster, phishing kits became automated, bot-driven credential stuffing became cheap, and password reuse became unavoidable. Meanwhile, helpdesk reset calls continued to eat into operational budgets.
Passkeys, based on the FIDO2/WebAuthn standard, solve the fundamental problem by eliminating the need for a shared secret. Without a password, there is nothing to phish, nothing to steal, and nothing to leak.
Through this blog, we explain why 2026 will be the tipping point, technically, operationally, and culturally, for enterprises to adopt a genuine password-less architecture finally.
Passwords have failed the Modern Internet
Today, almost every service, banking, shopping, travel, education, and government services are online. Users typically manage 20 to 50 different passwords. Many resort to weak passwords, reuse them across platforms and services, and often fall victim to phishing scams.
The consequence is severe:
- Widespread data breaches
- OTP related fraud
- Account takeovers
- Escalating helpdesk cost for password resets
Enterprises also realized that even with MFA, passwords remain the weakest link. This realization pushed the industry to seek a better approach, and that’s where passkeys come in.
Passkeys: What Are They?
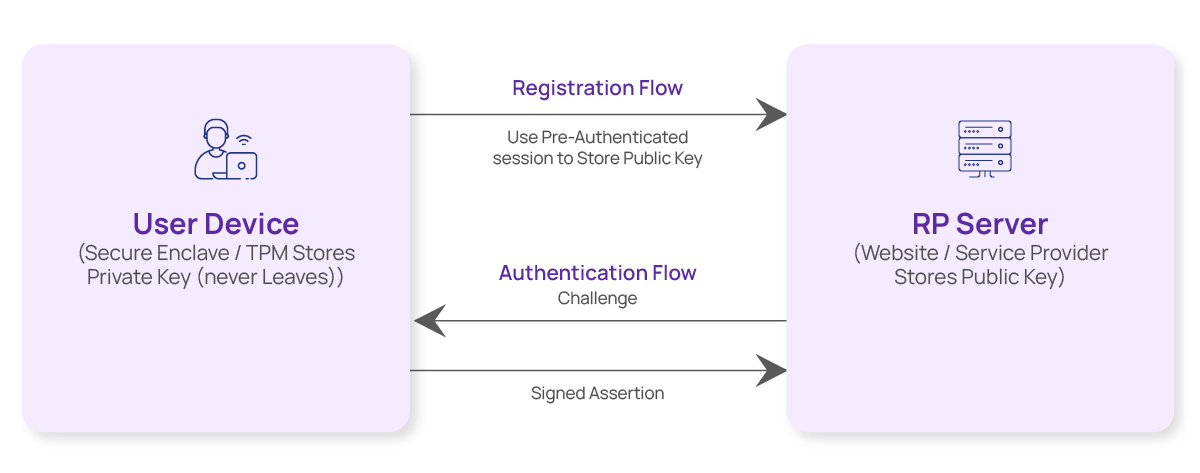
Passkeys rely on asymmetric cryptography. During the registration process, your device securely stores a private key and sends the public key, attestation, and metadata to the service provider’s website, which stores the corresponding public key. Passkeys are a form of FIDO authentication credential, built using open standards from the FIDO Alliance and the World Wide Web Consortium (W3C).
Here is the simplest visual:
The private key never leaves the device (Protected by Secure Enclave/TPM). When you log in, the service provider’s website or Relying Party (RP) server sends a cryptographic challenge. Your device signs this challenge using the private key, after biometric or PIN verification, and returns a signed assertion bound to the origin and domain.
This makes passkeys:
- Phishing-resistant (origin-bound signature).
- Replay-resistant.
- No credential leaks.
- No secret is shared with the server.
- No password databases.
- Bound to device and domain.
Passkeys aren’t just an upgrade to passwords; they replace the password model entirely.
FIDO2 is Finally Enterprise Ready
For many years, WebAuthn existed, but adoption lagged due to several gaps:
- Limited browser support
- Inconsistent mobile OS integration
- No cross-device passkey synchronization
- Poor enterprise documentation
- Unstable attestation formats
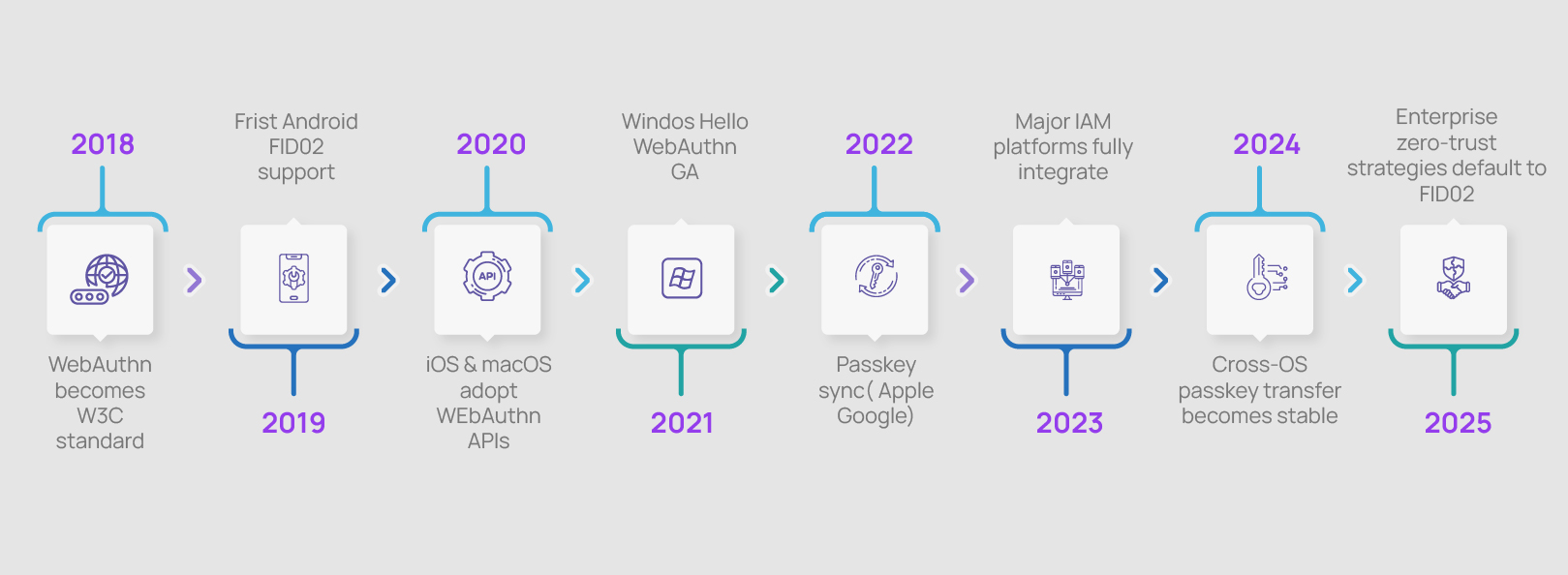
Between 2023 and 2025, these challenges were resolved as the FIDO2 [i] standard matured
FIDO2 Maturity Timeline [ii]:
By 2026:
- Leading Identity Providers – Okta, Azure AD, Auth0, and Ping rolled out or have plans to release production-ready passkey implementations.
- Both device-bound and synced passkeys became widely supported.
- Cross-platform libraries implementation is now supported by leading MDM providers like Apple, Google, Microsoft [iii].
- Hardware security modules like TPM and Secure Enclave have become standard across devices.
These enterprises can now safely eliminate passwords without disrupting legacy workflows.
The Mobile-First Shift: The Real Driver Behind Passkey Adoption
The world has already moved to a mobile-first way of living. Daily digital life revolves around mobile apps, biometrics, and frictionless authentication. In this environment, passkeys become the obvious next step.
Biometric login is already a deeply ingrained user behavior.
Passkeys extend that behavior to every digital touchpoint, securely.
For organizations, the business case is also clear:
OTP costs continue to rise, SMS-based fraud is increasing, and biometric hardware-backed authentication is far more secure. With secure elements like the TPM and Secure Enclave now standard across smartphones, passkeys align perfectly with how people already use devices.
Integration and Operability: Easier Than What IT Teams Expected
One of the biggest reasons behind the rapid adoption of passkeys in 2025 is that integration is no longer painful. What used to be a six-month migration is now a 2–3 sprint project. IAM platforms provide drop-in passkey widgets, embedded WebAuthn libraries, automated fallback strategies, and admin-level attestation support, making rollout straightforward. IT teams can start with high-risk groups, expand gradually, and even enable auto-enrollment for managed devices with clear recovery flows, without forcing users to remember passwords.
From an engineering and operations perspective, the benefits are significant: a 32% reduction in password reset tickets [iv], lower SMS OTP costs, better login success rates, and cleaner IAM policies. Passkeys align perfectly with Zero Trust principles and eliminate reliance on insecure, costly SMS OTPs. Native browser support and consistent WebAuthn APIs across platforms further simplify integration, supported by SDKs for Android, iOS, and the web. This reduced complexity helps large organizations adopt passwordless authentication more quickly, while improving mobile app conversion rates and the overall user experience.
Password Fatigue: The Emotional Problem That Nobody Talks About
Users today are overwhelmed by password fatigue. They juggle dozens of accounts, each with unique complexity rules, leading to constant resets and a growing fear of scams. The cycle is exhausting
Forget password → Reset → OTP → Create new password → Repeat.
Add to that phishing alerts and breach notifications, and it’s clear why frustration is at an all-time high.
Passkeys solve this with one simple principle: use the device you already trust. No more memorizing, no more guessing. Just tap your fingerprint or use face to unlock, and you’re in. This shift removes the headache and delivers a sense of relief factor that plays a bigger role in adoption than most companies admit. By eliminating passwords entirely, passkeys offer security and simplicity in one move, making them the obvious choice for a world ready to leave password chaos behind.
Beyond the Basics: Additional Drivers and Emerging Challenges
Passkey adoption in 2025 isn’t just about convenience; it’s backed by several powerful factors. Leading consumer brands like Google, Apple, Amazon, and Samsung are championing passkeys, building trust, and accelerating mass adoption. Enterprises benefit from reduced support costs as password reset calls decline, while tightening regulations in sectors like finance make phishing-resistant authentication a compliance advantage. Modern devices now come equipped with secure hardware (TPMs and Secure Enclaves), ensuring that private keys remain safe. Education and awareness campaigns further boost confidence in usability and security, and smart fallback strategies enable password use during the transition, easing migration without compromising safety.
However, challenges remain. Interoperability between ecosystems (e.g., Apple ↔ Android) can still be clunky, and fallback mechanisms may introduce vulnerabilities if not managed well. User education gaps persist, as not everyone understands public-key cryptography, and browser-level risks, such as malicious extensions, are under scrutiny. Legacy infrastructure also poses hurdles for enterprises with older systems. While these issues require attention, the momentum behind passkeys is undeniable, and the benefits far outweigh the risks.
Conclusion: Passkeys Are Taking
Passkeys mark a fundamental shift in how users authenticate, replacing the friction, risk, and limitations of passwords with a simpler, more secure, mobile-first experience. With the ecosystem maturing across devices, browsers, and enterprise tools, 2026 is set to become the tipping point for large-scale password-less adoption.
To summarize:
- Passkeys deliver phishing-resistant, hardware-backed security.
- 2026 signals the true beginning of widespread password-less authentication.
- A mobile-first world accelerates adoption through intuitive biometric login.
- The supporting ecosystem, OS, browsers, IAM, has become fully enterprise-ready.
- Users and businesses benefit from simpler UX and reduced password-related overhead.
While passwords won’t vanish immediately, their decline is now unavoidable as organizations move toward stronger phishing resistance, lower operational costs, and a seamless “tap and login” journey.
[i] https://fidoalliance.org/passkeys/
[ii] https://www.ibm.com/think/topics/fido2#1337304782
[iii]https://mobileidworld.com/apple-introduces-cross-platform-passkey-import-export-features-across-operating-systems/
[iv]https://fidoalliance.org/celebrating-world-passkey-day-2025-showcase-of-real-world-passkey-deployments/?utm_source=chatgpt.com