One of APAC’s leading regulatory body released a mandate that every bank under its jurisdiction must undergo Red Team Assessments for all critical systems facing the internet. These assessments can help banks identify vulnerabilities and business risks, and security controls by simulating an attacker’s objectives and actions.
The Challenge
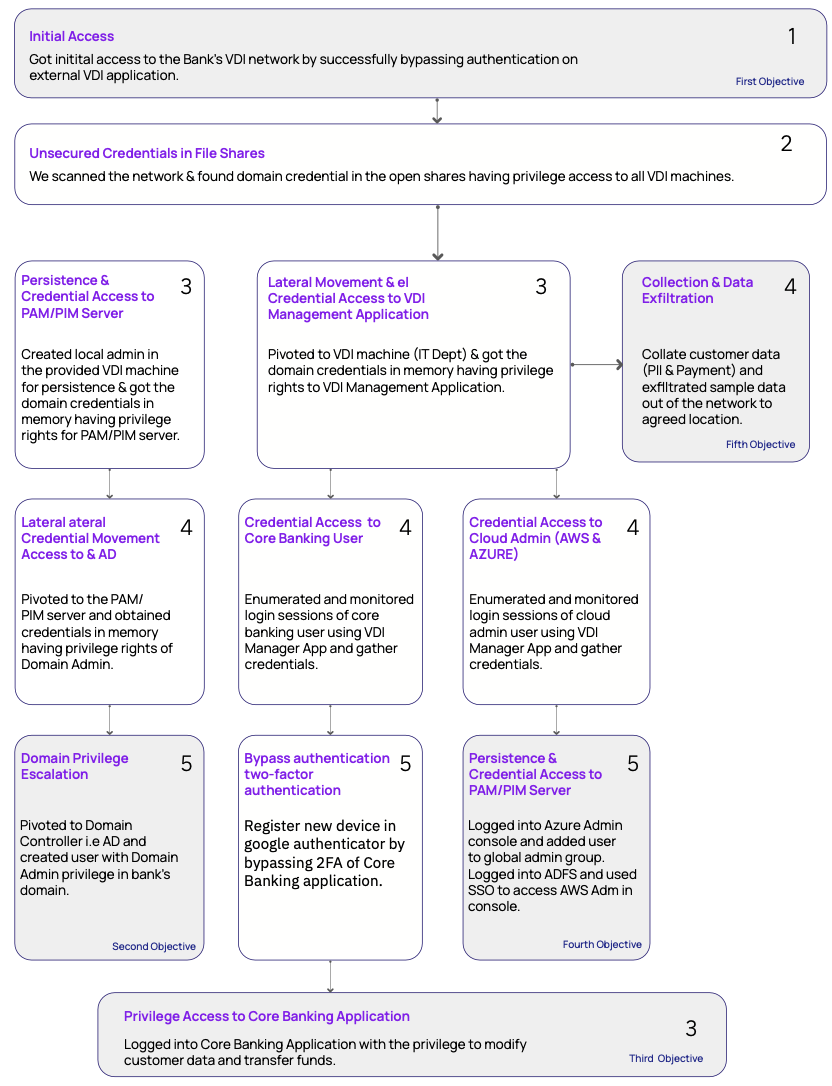
It was time for the bank to perform the Red Team Assessment to gain a better understanding of its existing flaws and assess the overall security posture. The banks also wanted to know whether their current security controls were robust to prevent/ detect against network intrusions, social engineering, and internal attacks on their network and Active Directory. The objective of this assessment was to identify potential security gaps in the bank’s network, get privileged access to critical infrastructure (Active Directory, Cloud console, Core banking applications), and access company sensitive data (Financial and PII data).
Strategy Design and Solution Approach
The Red Team Assessment leveraged the adversarial attack emulation in adherence to industry standard to Advanced Persistence Threats (APT) observed in millions of attacks that led to cyber breaches worldwide. The Red Team assessment performed for the bank employed both internal and external approaches. As a part of the external Red Team, the NuSummit Cybersecurity team used a complete Blackbox methodology, which meant that the team commenced their assessment without any prior knowledge. During the reconnaissance phase, the team uncovered a vulnerable endpoint within the VPN portal capable of circumventing Multi-Factor Authentication (MFA) by the addition of MFA devices for other users. By leveraging a combination of phishing attacks and compromised credentials sourced from recent security breaches, the team successfully bypassed the MFA controls within the VPN system, thus gaining unauthorized internal access to the client’s environment.
The Red Team assessment performed for the bank was an “Assume Breached” scenario that simulated targeted attacks through the tools, techniques and procedures used by real world adversaries. For this assessment, the bank provided NuSummit Cybersecurity with two low privilege domain user accounts having VDI access to the internal network. The assessment followed a stealthy, evasive approach to meet the defined goals and objectives.
Plan : Define scope, approach, objectives, ROE, boundaries, and limitations.
Key activities :
- Finalize engagement scope and objectives.
- Finalize communication guidelines, identify the project sponsor.
- Establish Rules of Engagement (ROE), boundaries, and limitations.
- Develop project plan, along with key milestones and periodic reporting timelines.
External Red Team: Intel collection, threat profiling, and gain foothold.
Key activities :
- Perform OSINT reconnaissance, active and passive scans.
- Define threat profile and attack scenarios based on information gathered via OSINT framework.
- Initial Access: 1. Social engineering attacks – phishing, vishing, etc 2. Client-side attacks 3. Server-side attacks.
- Execution
- Persistence
- Privilege Escalation
- Defense Evasion – Evade and bypass email gateway/Mail filter sandbox host/endpoint controls, security devices/solution, and SOC.
Internal Red Team: Gain access to critical assets, capture flags, and exfiltrate sensitive info.
Key activities :
- Initial access
- Internal recon
- Privilege escalation
- Defense evasion – Evade and bypass Host/Endpoint controls, network security devices/solutions.
- Lateral movement
- Collection
- Command and Control (C2)
- Objectives – 1. Gain possible privileged access to critical assets (Crown Jewels). 2. Capture flags and perform data exfiltration to the agreed location or C2 machine.
Deliverables: Gap documentation
Key activities :
- Document identified observations/gaps in defense controls/solutions with artifacts.
- Comprehensive report demonstrating the approach and output of each goal.
- MITRE ATT&CK mapping.
- SOC detection and prevention gap analysis.
- Provide short-term and long-term recommendations to detect and prevent the attacks.
- Lessons learned.
- Report presentation.
Outcomes for a Valuable Difference
Mitigation of existing risks
Evaluated the effectiveness of existing security controls and solutions to further optimize and further tune them to mitigate risks. Got a deeper understanding of the risk levels of the most critical assets in the organization.
Threat detection and response capability assessment
Evaluated the detection and response capabilities of Blue Team to improve the Security Operations Centre (SOC) maturity. Uncovered serious security flaws that would not have been detected with traditional penetration tests.
Security posture improvement
Provided an evidence-based risk profile to senior management and gave recommendations to improve the overall security of security investments.
Objectives Achieved as a Part of the Solution Framework
Unauthorized internal access to the client’s environment
- The Nusummit Cybersecurity Team identified user credentials by leveraging a combination of phishing attacks and compromised credentials sourced from recent security breaches.
- They were able to bypass two-factor authentication on the VPN console.
Compromise the Active Directory of the highest privileged account
- NuSummit Cybersecurity Red Team experts compromised the highest privilege account: the Domain Administrator account.
- They added a rogue Domain Administrator in the bank’s domain.
Upon accessing payment systems, modify customer data and perform a transaction
- The team bypassed the two-factor authentication mechanism of the Core Banking application.
- They modified customer details in the Core Banking application.
Access VPC servers, ensure compromise of the VPC Admin and make configuration changes to the VPC
- The team got privileged access to the bank’s Azure and AWS environments.
- They added a rogue Global Administrator to the Azure environment.
Exfiltrate customer and card information
- The team accessed financial data and PII data ((Aadhar, PAN, Passport, bank statements etc.).
- They exflltrated dummy data externally to the NuSummit Cybersecurity controlled Command and Control server.
Solution Highlights
The high-level description of the attack path to complete the assessment objectives is demonstrated below