Risk-Aware IAM
Secure digital identities and applications, ensuring legitimate user and identity access
Secure digital identities and applications. Ensure legitimate user and identity access.
Home / Risk Aware IAM
Legacy IAM systems are often used as IT administration tools instead of leveraging them as effective security and risk management solutions. These systems lead to unmitigated access risks, failed audits, an increase in access misuse incidents, and a loss of confidence in IAM programs. With the rise in attack surfaces, organizations must shift their view of IAM as a critical security control. They should focus on developing a risk-aware IAM approach to address security flaws and proactively meet privacy and compliance requirements.
Risk-aware IAM can support your business with these advantages:
- An integrated view of identities across applications and business functions.
- Enhance visibility and control over system and application users.
- Institutionalization of best practices, policies, and procedures to meet compliance needs.

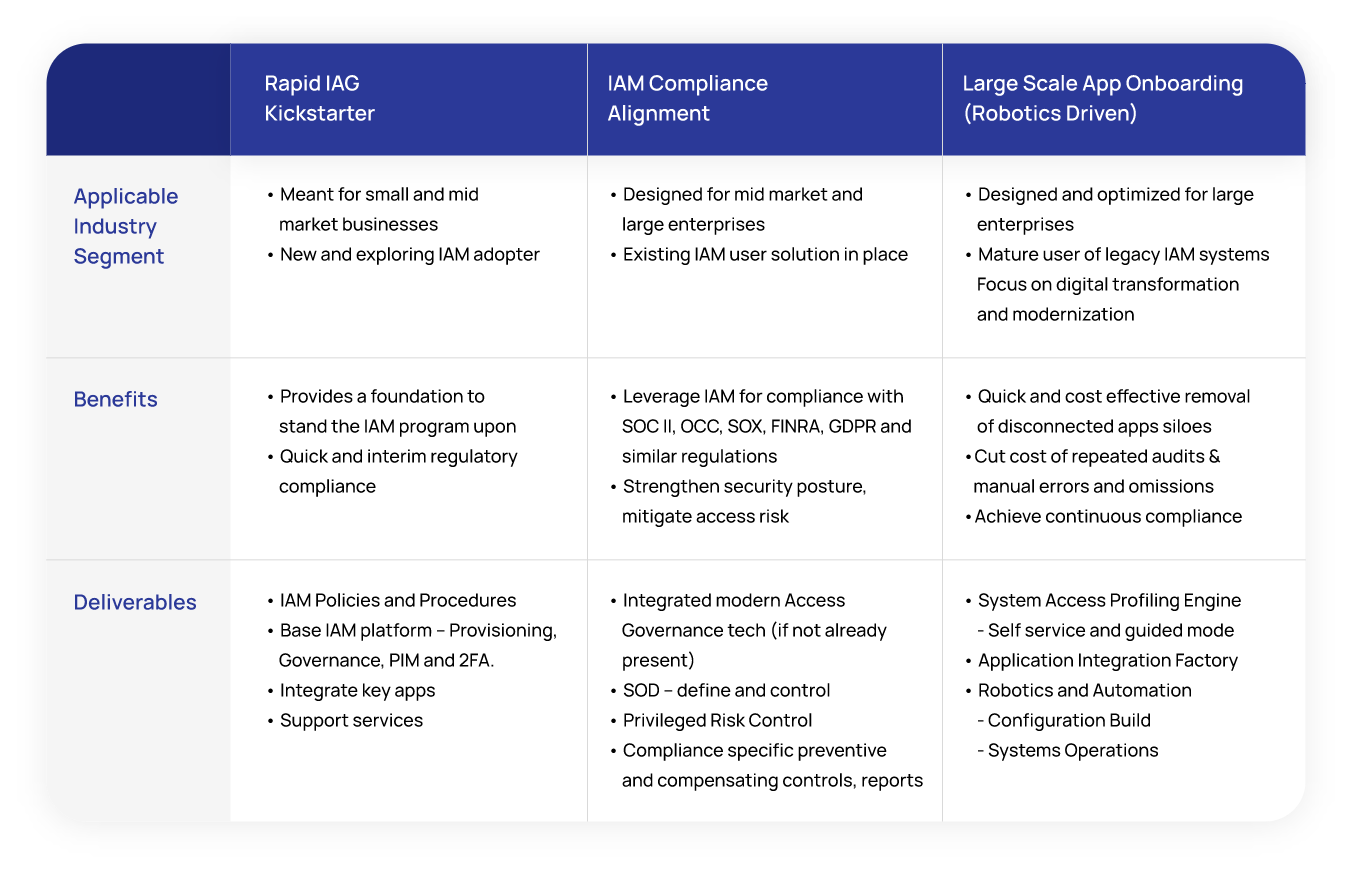
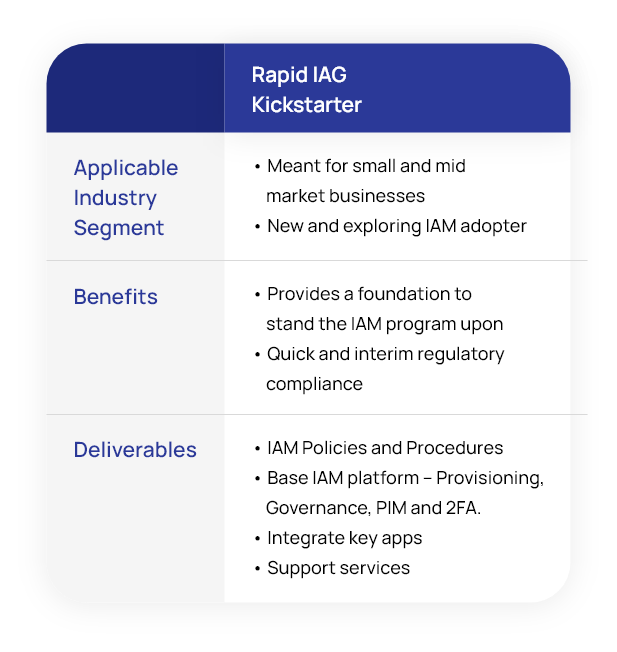
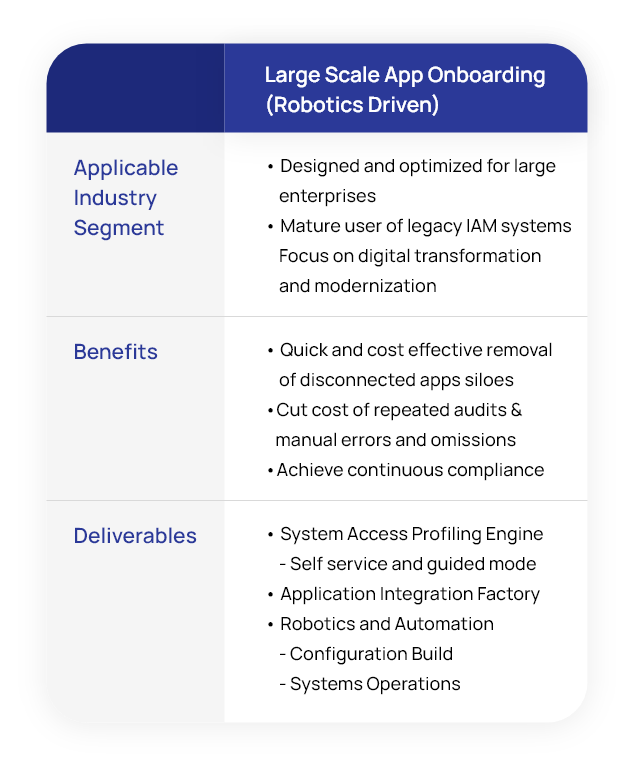
Risk-Aware IAM Offerings
NuSummit Cybersecurity’s risk-aware IAM services enhance enterprise capability to mitigate risks, reduce threats, and ensure continuous compliance by enforcing policies needed to drive business processes. The service intent is to transform legacy IAM solutions to make them risk-aware. Transformation also includes establishing relevant policies and procedures to drive risk-based authentication methods and ensure the right user access.
Read the Risk-Aware IAM Whitepaper
Risk-Aware IAM Transformation Methodology
Risk Aware IAM Transformation – Methodology
Integrated access reviews with provisioning.
Rapid app integration with identity and governance platform to eliminate silos.
Segregation of Duties (SoD) definition and control setup.
Role encapsulation.
Compliance specific controls and reports.
Risk-aware IAM is a crucial imperative for businesses while adopting newer technologies to sustain a competitive edge and deliver better value to customers. As organizations grow, their infrastructure is likely to scale and accommodate diverse users and access points. They want greater agility in securing user access and credentials to reduce operational complexity and ensure compliance.
NuSummit Cybersecurity offers services and solutions for organizations of various sizes and scales, enabling them to accommodate the dynamic growth of user access and identities.
Experts in securing software development ecosystems


- Prepare an inventory of Roles and Entitlements.
- Prepare a list of Entitlement Groups.
- Classify the Roles and Entitlements in Groups.
- Generate a sample set of Toxic Combinations.
- Optimize the sample set.
SoD Modeler
NuSummit Cybersecurity’s SoD modeling solution helps businesses identify and mitigate toxic combinations through a built-in list of security compliance requirements. It also supports multiple use cases such as:
1
SoD matrix based on business roles (for applications integrated with IAG).
2
SoD matrix based on entitlements (for applications not integrated with IAG).
3
SoD matrix based on business processes (for process-based cross-application SOD).
NuSummit Cybersecurity’s Risk-aware IAM services can enable you to deploy transformative solutions that can strengthen access governance and are scalable to your process and business needs.
- Automate access request workflows and check Segregation of Duties (SoD).
- Centralize user authentication, including provisioning and de-provisioning of users.
- Meet regulatory requirements through multifactor authentication and ensure secure access.
- Context-aware services to prevent oversight and protect data.
- Protect your infrastructure and mitigate business risks.